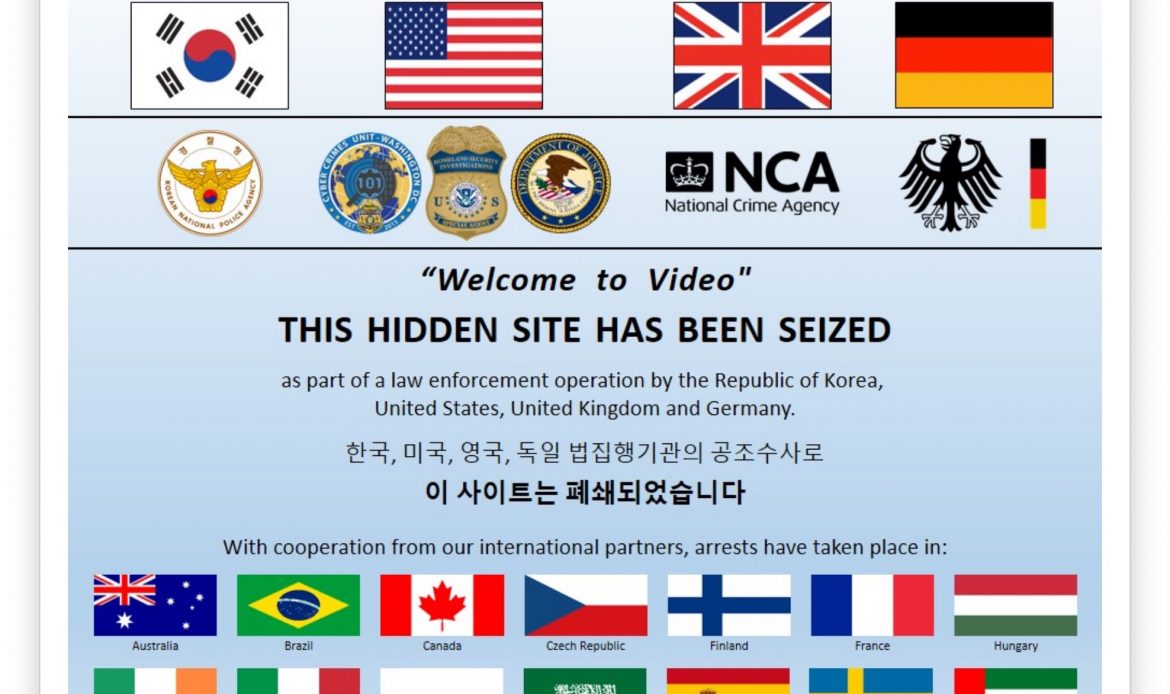
The Justice Department launched charges in the direction of the net admin and tons of of prospects of the “world’s largest” child sexual exploitation market on the dark web/TOR.
In November 2017, Bryce Durbin was working for CBS as the security editor at ZDNet. A hacker group reached out to him over an encrypted chat claiming to have broken proper right into a dark web site working a big child sexual exploitation operation.
The group claimed it broke into the darkish web site, which it talked about was titled “Welcome to Video,” and acknowledged four basic server IP addresses working the positioning. They moreover equipped him with a textual content material file containing a sample of about one thousand IP addresses of individuals who they talked about had logged in to the positioning with out the shoppers information.
Bruce’s editor-in-chief talked about how the dark web site was already beneath federal investigation, and writing about it would jeopardize that effort. He moreover talked about “There was no legal way we could access the site to verify it was what the hackers claimed.”
The hackers gave him a particularly created username and password for the positioning, which they talked about was created just for him to verify the claims. But they may not entry the positioning for any goal — even for journalistic causes. So he decided to report the data to the FBI whereas defending the sources. Nothing was heard once more from the FBI for awhile; until recently (two years later). But once more to some very fascinating data:
They found individuals accessed the darkish web site from the networks of the U.S. Army Intelligence, the U.S. Senate, the U.S. Air Force and the Department of Veterans Affairs, along with Apple, Microsoft, Google, Samsung and a quantity of different universities throughout the world. We could not decide, nonetheless, specific individuals who accessed the positioning. They merely used who.is for these IP’s they’d.
U.S. prosecutors talked about in the indictment, filed in August 2018 nevertheless unsealed Wednesday, that the dark web site — confirmed as “Welcome to Video” — had some 250,000 user-uploaded graphic pictures and videos of children who had been being sexually abused. The authorities known as it the “largest darknet child pornography website” in a press release.
After data of the positioning’s eradicating had been reported, The screenshot above was the TOR hidden deal with and the seized model on the internet website being displayed. According to the indictment, federal brokers began investigating the positioning in September 2017, two months sooner than the hackers breached the positioning. The site’s administrator, Jong Woo Son, had been working the operation from his residence in South Korea since 2015.
The indictment talked about the first landing net web page to the positioning contained a security flaw that enable investigators uncover some of the IP addresses of the TOR web site — simply by right-clicking the online web page and viewing the availability of the site.
It was a critical error, one that can set off a collection of events that can ensnare your total site and its prospects.
Prosecutors talked about inside the indictment that they found a quantity of IP addresses: 121.185.153.64 and 121.185.153.45. One of the IP addresses the hackers gave him was 121.185.153.114 — an deal with on the equivalent neighborhood subnet as the web site.
It was long-awaited affirmation that the hackers had been telling the fact. They did the reality is breach the positioning. But whether or not or not or not the federal authorities knew regarding the breach stays a thriller.
It’s believed the indictment was saved beneath seal until after the individuals suspected of caring inside the site had been arrested.
In entire, there have been 337 arrests, along with a former Homeland Security specific agent and a Border Patrol officer.
Authorities had been able to rescue 23 children who had been being actively abused.
Bryce reached out to the federal brokers, and was suggested the FBI was not involved inside the investigation. The Internal Revenue Service’s Criminal Investigation division, and the Homeland Security Investigations unit, had been these working the case. IRS obtained an anonymous tip that leap started the investigation.
While authorities from the U.Ok. and South Korea moreover contributed to the investigation. The IRS used know-how to trace bitcoin transactions, which the dark web site used to income from the child exploitation videos. Users should pay in bitcoin to acquire content material materials or add their very personal child exploitation videos. The authorities moreover launched a civil forfeiture case to seize the bitcoins allegedly utilized by 24 individuals in 5 nations who’re accused of funding the positioning.

