The Stuxnet virus that decimated Iran’s nuclear program was introduced by a Dutch mole working with the CIA and Mossad, intelligence sources claimed, as Israel is shopping its cyber weapons to anyone with cash to buy.
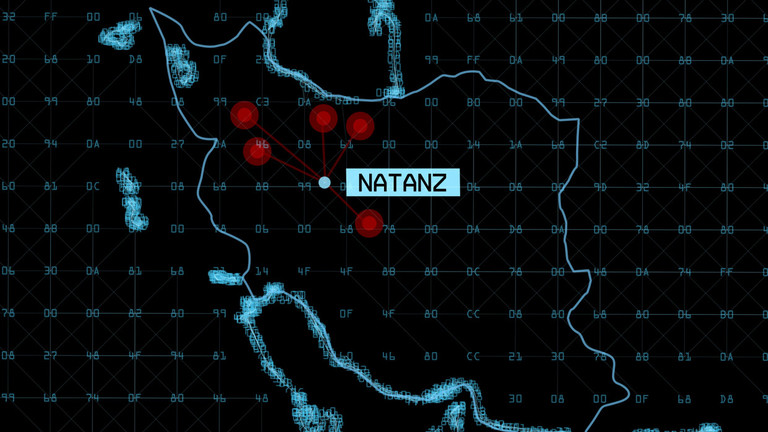
An Iranian engineer was recruited by the Dutch intelligence agency AIVD, acting under the direction of the CIA and Mossad, to infect some 2,000 Iranian nuclear centrifuges with the catastrophic Stuxnet virus, which set that country’s nuclear program back years, according to intelligence sources who spoke to Yahoo News.
The mole, who posed as a mechanic, reportedly provided data that was critical to helping the virus’ developers shape their code to specifically target the systems at the Natanz plant where it was ultimately unleashed, then helped get the virus onto the plant computers using a flash drive. One of the sources called him “the most important way of getting the virus into Natanz.”
While the US and Israel were the primary players behind the initiative, designed to cripple but not destroy Iran’s nuclear program in order to force it to the negotiating table, the Netherlands, Germany, and one other country (believed to be France) were also allegedly involved, motivated by Israel’s insistence that Iran was developing a nuclear bomb. In addition to supplying the agent, the Dutch contributed information about the centrifuges, which were based on designs stolen from a Dutch company in the 1970s by a Pakistani scientist.
Stuxnet is widely considered to be the first offensive cyberweapon, launching a “digital arms race” after a new and especially virulent version of the code, reportedly deployed by Mossad against US advice, was brought in by unsuspecting contractors who’d been infected elsewhere after the mole lost his access to the plant. That code not only infected other companies the contractors worked with but spread to thousands of computers worldwide, bringing Stuxnet to public attention by June 2010. The exposure of the virus triggered a paradigm shift in cyber operations and set other countries – including the US’ enemies – clamoring for their own cyberweapons.
Since then, Israel has capitalized on its reputation as one of the prime movers behind the deadly (for computers, at least) virus, selling cyber weapons to countries around the world. And it’s about to get much less particular about whom it sells those weapons to, causing significant concern among cybersecurity and human rights groups who have already accused Tel Aviv of marketing insidious spyware like NSO Group’s Pegasus to repressive regimes who use it to spy on opposition politicians, human rights activists and even journalists.
These abuses occurred under a system that required 12 months or longer to approve cyberweapons sales, with matters further complicated by marketing and export license requirements and sales restricted to tightly-vetted allies. Under the new system, purchases can be approved in as little as four months, and more companies will be eligible to obtain the licenses. More ominously, a larger pool of potential buyers will have access to the devastating cyberweapons.
The Israeli Defense Ministry has justified loosening restrictions by insisting Israeli companies need the freedom to remain competitive in the industry, in defiance of a United Nations call for a global moratorium on cyber weapons sales.

